Nonprofit Accounting Basics
Remote Work Reinforces the Need for Appropriate Cybersecurity
The abrupt shift to virtual operations during the COVID-19 pandemic exposed the vulnerabilities of some nonprofit organizations and resulted in a painful ‘lesson learned’ for others. Although employees will be allowed to return to the office in 2021, working from home in some form appears to be here to stay. Leadership must recognize that this puts their organizations at greater risk for security breaches and take proactive steps to protect their data assets. No group of organizations is more vulnerable than the small nonprofit organizations that provide critical services to our local communities and fill the gap when government funding is not available.
Prioritizing cybersecurity
Hackers are becoming more sophisticated every day. Not only are cybersecurity breaches constantly changing, criminals have capitalized on the increased number of end-user points with the popularity of remote work. Cyber criminals don’t care about your mission and they are not empathetic to your budget constraints. While finding it difficult to stretch limited resources even further, smaller nonprofits must make critical investments in cybersecurity and adopt the proven best practices of larger organizations. Without proper cybersecurity, the organization’s critical activities are at risk and the potential for reputational damage is real.
Characteristics of successful cybersecurity programs
Successful cybersecurity programs include a combination of these elements.
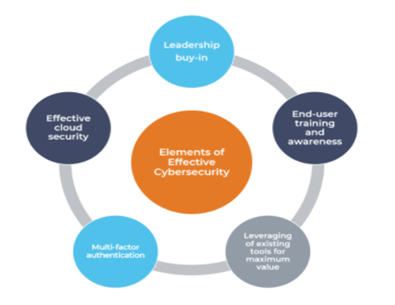
Leadership buy-In
Arguably, one of the most important aspects of cybersecurity for a nonprofit organization is leadership buy-in and support. While effective cybersecurity to protect the organization may seem like an obvious priority, in many cases there are detrimental enforcement issues. The cybersecurity “shield” may be in-place, but exceptions are made for specific users creating a weakness in the organization’s security posture. Common examples of these exceptions include exemption from the password policy, exclusion from multi-factor authentication or failure to complete cybersecurity training. Leadership support allows the organization’s information technology (IT) team to enable the appropriate cybersecurity measures and enforce critical policies and procedures.
End-user training and awareness
Equally important as leadership buy-in, end-user training and awareness is essential to the success of every cybersecurity program. While many organizations have employed spam filters, the best technology products still cannot stop every phishing attack. Even before the pandemic, Verizon’s 2019 Data Breach Investigation’s Report stated that 94% of malware was delivered via email. Additionally, Symantec’s 2019 Internet Security Threat Report reported, “65% of groups used spear-phishing as the primary infection vector.” With email being the main form of communication, it is critical to have continuous education for end-users. With an effective cybersecurity training and awareness program, all users are held to the same standard. This includes everyone from the C-suite and the IT department to anyone accessing the organization’s network resources.
Leveraging of existing tools for maximum value
When organizations get serious about cybersecurity, the conversation typically starts with a well-publicized breach and/or introduction to an advertised product or service. Contrary to popular belief, you do not need to spend a lot of money to protect your organization. Start with reviewing the products and services already in use and evaluate whether these existing solutions are being deployed to their full potential. For example, does your organization require password complexity? Does it require passwords change after a certain period? Is there a policy that will lock the account after a pre-set number of failed login attempts? Many existing security features are disabled for convenience, but they can leave a large gap in your organization’s cybersecurity posture.
Implementation of multi-factor authentication
One of the best values among the services available for cybersecurity is multi-factor authentication. Multi-factor authentication requires a second confirmation of the identity of the person accessing the system. For it to protect the organization though, all entry points into the network must require this additional form of authentication. If your organization currently uses Microsoft Office 365, multi-factor authentication is included in your license. Otherwise, there are multi-factor solutions for purchase including Duo, RSA and Yubikey. A little research will go a long way to ensure your peace of mind that the organization’s network has protection.
Effective cloud security
You have moved everything to the Cloud, so your cloud provider now handles your organization’s cybersecurity. Not so fast! Even though Amazon Web Services, Azure or Google Cloud is supplying infrastructure as a service, your organization is still responsible for configuration and proper set-up. They will not manage your operating system updates, nor will they lock down your network. In addition, if your configuration is incorrect, your data can be open to anyone online.
Cloud services are complex and very powerful, but misconfigurations can be catastrophic. By default, newly created S3 buckets in AWS block public access, but this was not always the case. According to security firm Skyhigh Networks, 7% of all S3 buckets (storage in AWS) have unrestricted public access and 35% are unencrypted. Some of these storage buckets have intended unrestricted access, but many customers are unaware that they are not protected. In addition, just because public access is initially blocked by default does not stop someone from changing the access level later.
There is also an important distinction between internally managed IT vs. a managed service provider (outsourced IT) when it comes to cybersecurity. Regardless of whether IT is internal or outsourced, an independent assessment should be conducted annually to determine that cybersecurity risk is being handled and mitigated appropriately. You cannot rely on the assurance of an outsourced provider. Although there may be a substantial benefit gained from outsourcing to third parties, it is still your responsibility (and of the utmost importance) to assess your cybersecurity on an annual basis. Your organization is responsible for verifying the security of your systems and data, otherwise known as Third-party Risk Management.
Next Steps and Resources
The elements described above should be part of every nonprofit’s security arsenal to prevent a potential cybersecurity breach. Many of these elements may already be present in your organization awaiting deployment. While this list is not all-inclusive, it includes proven industry best practices and can serve as a strong starting point for any organization concerned about cybersecurity.
Ransomware Attacks
Ransomware victims should immediately contact their local FBI field office to request assistance, or submit a tip online. Victims are also encouraged to file a report with the FBI’s Internet Crime Complaint Center (IC3).
Should your organization pay the ransom?
This is an evolving area and organizations should take note of several factors before responding.
While the FBI generally does not recommend paying the ransom, there are instances where the agency has advised organizations to satisfy their attacker’s demands. Your cybersecurity incident response plan should include a worst-case scenario that includes the possibility of paying a ransom to retrieve your data. Unfortunately, paying the ransom does not guarantee your data will be returned. It also encourages perpetrators to target additional victims and inspires other bad actors to get involved. Contact the FBI and your cybersecurity insurance provider to weigh all considerations before responding to a ransomware attack.
Case study: Proactive Cybersecurity Measures Prevent Ransomware Attacks
A 501(c)(3) organization based in Washington, DC found out the hard way that remote work poses a significant security risk. The organization first discovered an issue on a Friday night in mid-April 2021 when a team member noticed some of the $10M organization’s files had become encrypted. Although the organization’s IT team moved quickly and the threat actor lost access by Saturday morning, the damage was done. By Monday morning, the organization realized they had fallen victim to a ransomware attack. Leadership moved quickly to inform their employees and the board of directors about the breach, and they contacted their cybersecurity insurance provider and the FBI to report the incident.
Damage to the organization
As a result of the breach, the organization lost access to all files on their servers which included data associated with their programmatic work. The threat actor also emailed others in the organization’s network to urge the victim organization to pay the ransom. Due to the encryption, the organization lost access to their daily backups as well. They were forced to restore their data from an off-site backup which resulted in a loss of 6-10 weeks of work.
By late May, the organization was up and running again but they were still downloading data from the off-site backup. At that point, the challenge shifted from restoring the data to providing team members with clean equipment. Not only were employees working from home, the pandemic also posed issues for purchasing and shipping new equipment.
Quick action minimizes damage
Damage to the organization could have been much worse. Fortunately, they had some data in cloud-based systems and their email and website were not impacted. They also had an alert and well-trained IT team who acted quickly and minimized damage. To head off any legal ramifications, leadership notified the board of directors promptly which provided a key referral to a cybersecurity attorney. Finally, the organization had invested in a good cybersecurity policy which provided financial reimbursement and access to the experts needed for forensics and recovery.
Lessons learned
While the damage was minimized, the ransomware attack still provided some tense moments for the organization’s leadership and employees. As a result, the organization is planning some critical updates to their cybersecurity policies and procedures to prepare the organization for future breaches.
Proposed changes include:
- Developing a business continuity plan. A business continuity plan helps organizations prepare for emergencies by outlining the procedures to follow and assigning responsibility. Knowing how to respond and who to contact for help during an emergency saves valuable time and minimizes possible damage.
- Revisiting cybersecurity policies and procedures. Technology changes are challenging for many people and it’s tempting to skip or relax best practices such as password complexity, multi-factor authentication and third-party risk management. Strong policies and procedures combined with internal training and education are your best bet to avoid a cybersecurity event. As a best practice, organizations should also perform an independent cybersecurity assessment annually to validate their current security and privacy posture.
- Developing an emergency communications plan. Whether it’s a stand-alone document or part of the organization’s business continuity plan, an emergency communications plan helps organizations control the narrative and minimize reputational damage. Communicating appropriately with your stakeholders should be just as important as forensics and recovery.
- Updating and testing the disaster recovery plan. A recovery plan is great – unless it does not work. Many organizations would be significantly damaged by the loss of 6-10 weeks of work. Add the many weeks needed for data recovery and most would be paralyzed. Consider how long your organization could survive without critical data. Understanding your current RTO (recovery time objective) will allow you to find the right balance of cost and potential downtime for your organization. Once you have updated your disaster recovery plan, test it regularly! Testing your disaster recovery plan is critical to ensuring it does not become obsolete.
- Updating the organization’s electronic file retention policy. The ransomware attack exposed the large amount of data the organization had accessible. Per the General Data Protection Regulation (GDPR), data should be retained only for as long as required for the primary purpose for which it was collected. For example, a tax return should only be kept for 7 years because the IRS has the right to audit up to that point. When in doubt, your cybersecurity insurance company should have guidelines for each type of data.
Small nonprofit organizations are not immune to cybersecurity risk and cannot afford to overlook the possible harm, particularly with many employees working from home. Contact an advisor who specializes in cybersecurity and privacy to assess your organization’s current cybersecurity posture. The cost of preparing your organization to withstand a cybersecurity event pales in comparison to the cost of data recovery and damage to your reputation.




